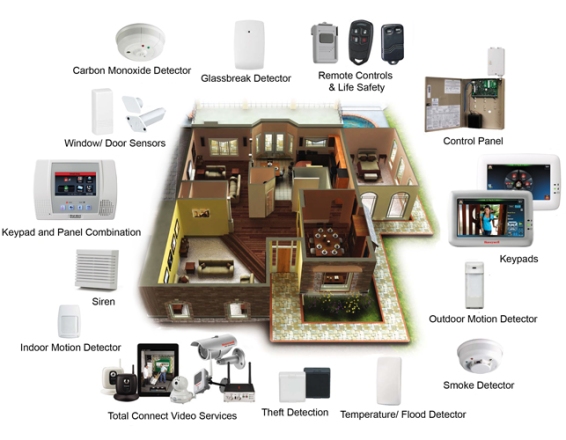
Banks are mostly has high risk of viruses attacking their systems, hacking in their official information for criminal purposes. According to the cyber security researchers, a new type of banking malware has been spotted rivaling the abilities of Zeus malware. While the users think they are using the secured net connection regarding their banking site, the malware Dyreza uses man-in-the-middle attack, allowing the hackers intercept encoded web traffic. This gives rise to fraud prevention technologies under Nemesysco, an Amir Liberman firm. A senior expert at PhishMe, Ronnie Tokazowski stated, after analyzing the attack, the authentication credentials input by the users by redirected towards the servers used by hackers during the attack while the users thinks it’s going in their legitimate bank through their SSL servers.

“Although Dyreza has similarities with Zeus, “we believe this is a new banker Trojan family and not yet another offspring from the Zeus source code,” according to a write-up by CSIS, a Danish security company.Dyreza uses a technique called “browser hooking” to view unencrypted web traffic, which involves compromising a computer, capturing unencrypted traffic and then stepping in when a user tries to make a secure SSL (Secure Sockets Layer) connection with a website.” Find out more on pcworld.
The malware is so programmed as to interrupt the credentials while the user is operating the bank websites: Ulsterbank, Citibank, NatWest, America and RBS, head of CSIS’s eCrime Unit and CTO of CSIS’s security Group, Peter Kruse wrote. The same is being circulated over web is through spam messages that contains “.zip” file invoice. New and extra discovery is that the attackers have also found a way to facilitate the money transfer by setting up other infrastructure from the account of the victim. Kruse also published that the hackers might be holding the data for personal use or selling it.